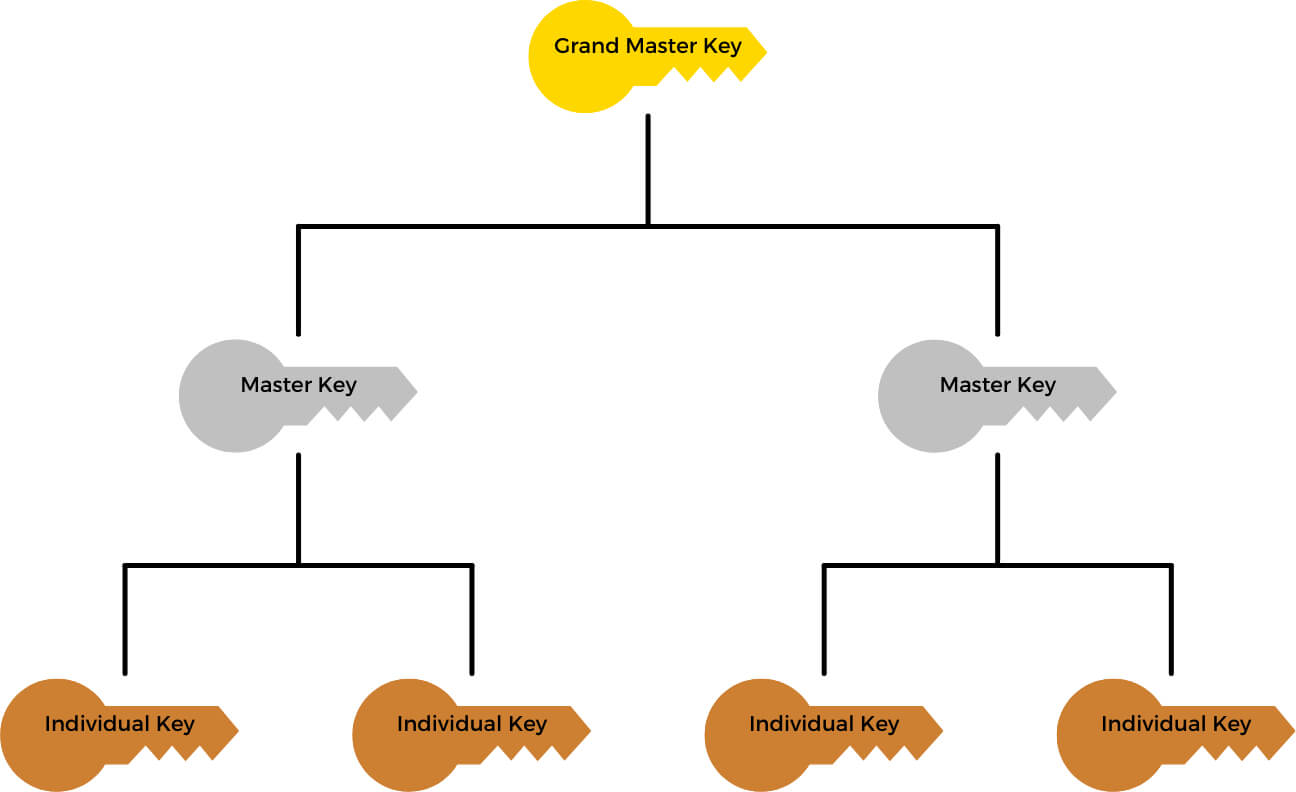
A master key system provides hierarchical access to locks across your organization, allowing authorized personnel access to different sections of your company. However, it can give a false sense of security if not correctly implemented. While a system may seem adequate initially, it may prove insufficient as it expands or in the event of key loss. Let’s explore best practices when selecting and implementing your master key system.
Access Control Requirements
To ensure effective management of master keys, start by carefully assessing your property and identifying entry points to different areas such as offices, departments, and data centres. Also, identify the key user categories in your organization. This step helps to outline key holders and users and establish the ideal key hierarchy.
Once you have this information, allocate access restrictions, especially to individuals who shouldn’t access high-security areas.
Limit Master Keys
When setting up your master key system, restrict master key access to those who only need it, while providing more specific access to other key holders.
Additionally, consider grouping master key access to single locations, similar entry points, or other organizational groups. This approach helps minimize the risk of a single master key having complete access across your organization. Carrying multiple keys can be inconvenient, but dealing with a lost master key that only has access to a few locations is far less demanding than one with access to every location. This can significantly reduce the time, money, and stress associated with rekeying.
Key Tracking Record
In a master key system, each key should be assigned specific serial numbers, and a detailed record should be maintained. This record should keep track of the master key system layout, the security access levels associated with each key, lock changes, and the individuals granted assigned keys along with the issued date.
For organizations with few keys to track, using a paper log or a spreadsheet can be effective. For larger organizations with many key holders and different access levels, using specialized tracking software is recommended. This software can help you keep track of all keys, key holders, and access levels in a more organized and efficient manner. Whichever method you choose, it is important to regularly maintain and update your documentation. This includes adding new keys as they are issued, removing keys that are no longer in use, and updating access levels as needed.
Restricted Master Key Systems
A critical aspect of a secure master key system involves using restricted keys. These types of key blanks are not available in stores. When you use restricted master keys, they can’t be copied by local stores or locksmiths without your permission. If you use keys that anyone can copy, your master key system becomes at risk of security breaches, and you have little control over stopping them.
This article outlines points to consider when choosing and using your next system. For more details on master keys, reach out to us today.